Users and Security
For your generated application, you will manage user access to the application though the provided Security Manager.
Applications generated on Foolproof Coding have the option to be generated with User Self Registration. In that case, when the user registers, their credentials are stored in the JGSEC Security Database automatically.
The system security user will need to first assign necessary permissions to self-registered users before the system will permit access to protected resources.
The Security Manager permits the creation of new users and groups, and definition of their access rights.
The Security Manager also permits changing the access mode of forms from Group to Submitter and vice versa.
Public access cannot be changed to Submitter or Group access. It remains Public as generated.
The Security Manager is provided as a deployable .war file, seperate to the generated application, with it's own .sql script for database and related object creation.
Should you generate multiple applications, and deploy them to the same Tomcat Server, they will all be managed by the one Security Manager.
Users are defined once in the security manager, and can be assigned to multiple groups across multiple generated applications.
The Security Manager is used to manage user access to multiple generated applications from Foolproof Coder. This shows the JGSEC application, which controls user access to itself, and in this case the Generator instance, XDBiM. All your generated applications will be listed here in your Security Manager.

Each managed application will have a single Security Map. This defines the access modes to each table comprising the generated application.
Table access is one of two mutually exclusive modes : Group or Submitter.
Group mode on a table means the access permissions apply to a Group. All users assigned to the group inherit the group access rights, which may be read-only or read-write.
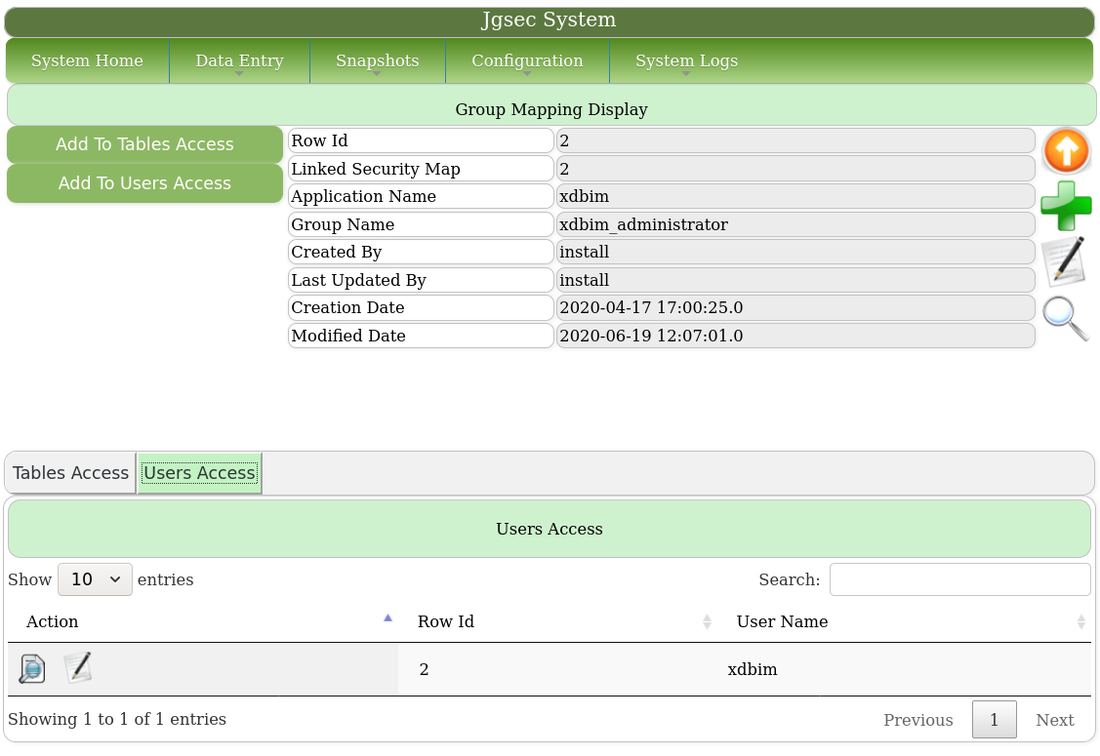
This is the actual security map for the Foolproof Coding generator application. There is only one group with access, xdbim_administrator.
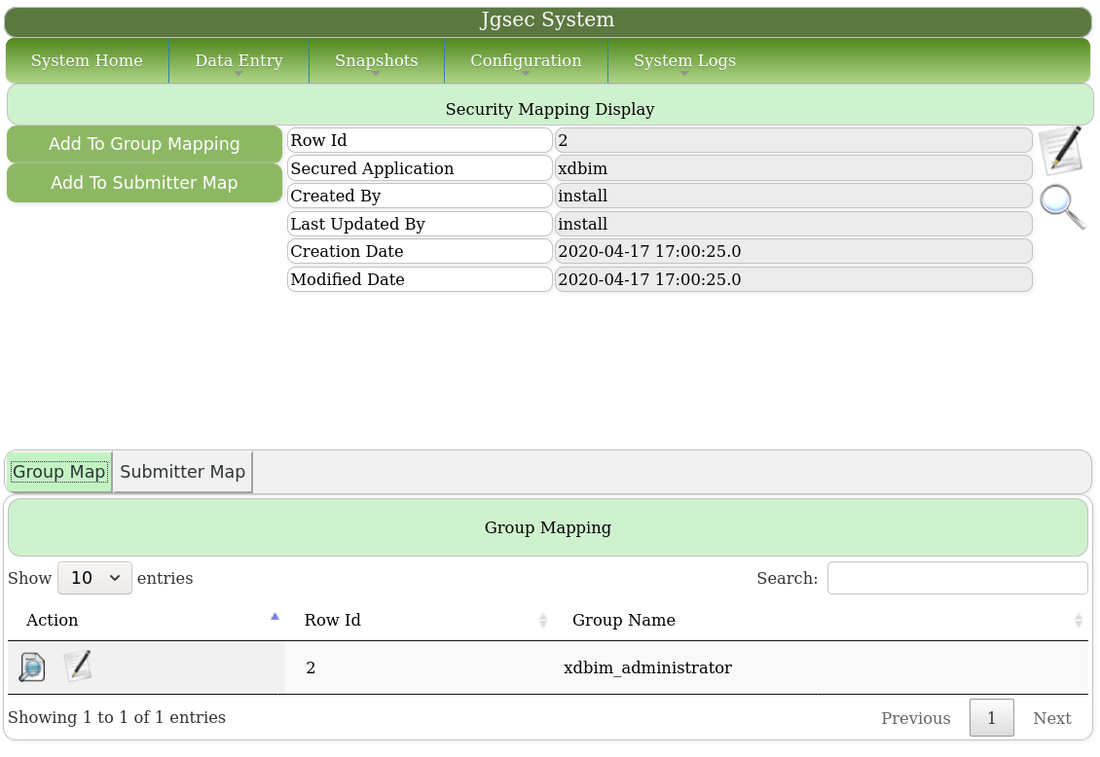
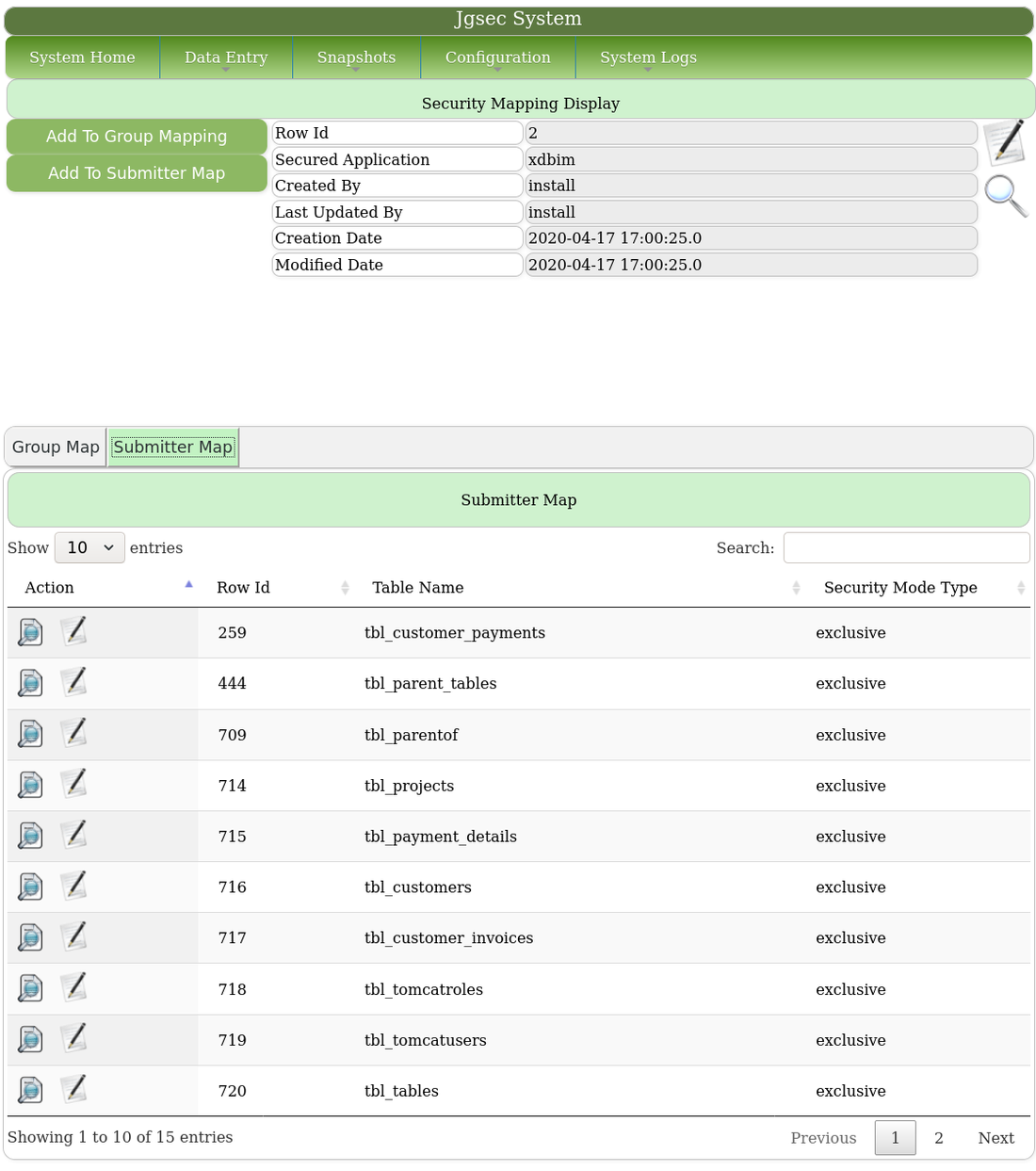
These are the tables in Submitter Mode, where users have exclusive access to rows which they create only.
These are the tables the group has access to, in exclusive mode, or with full permissions.
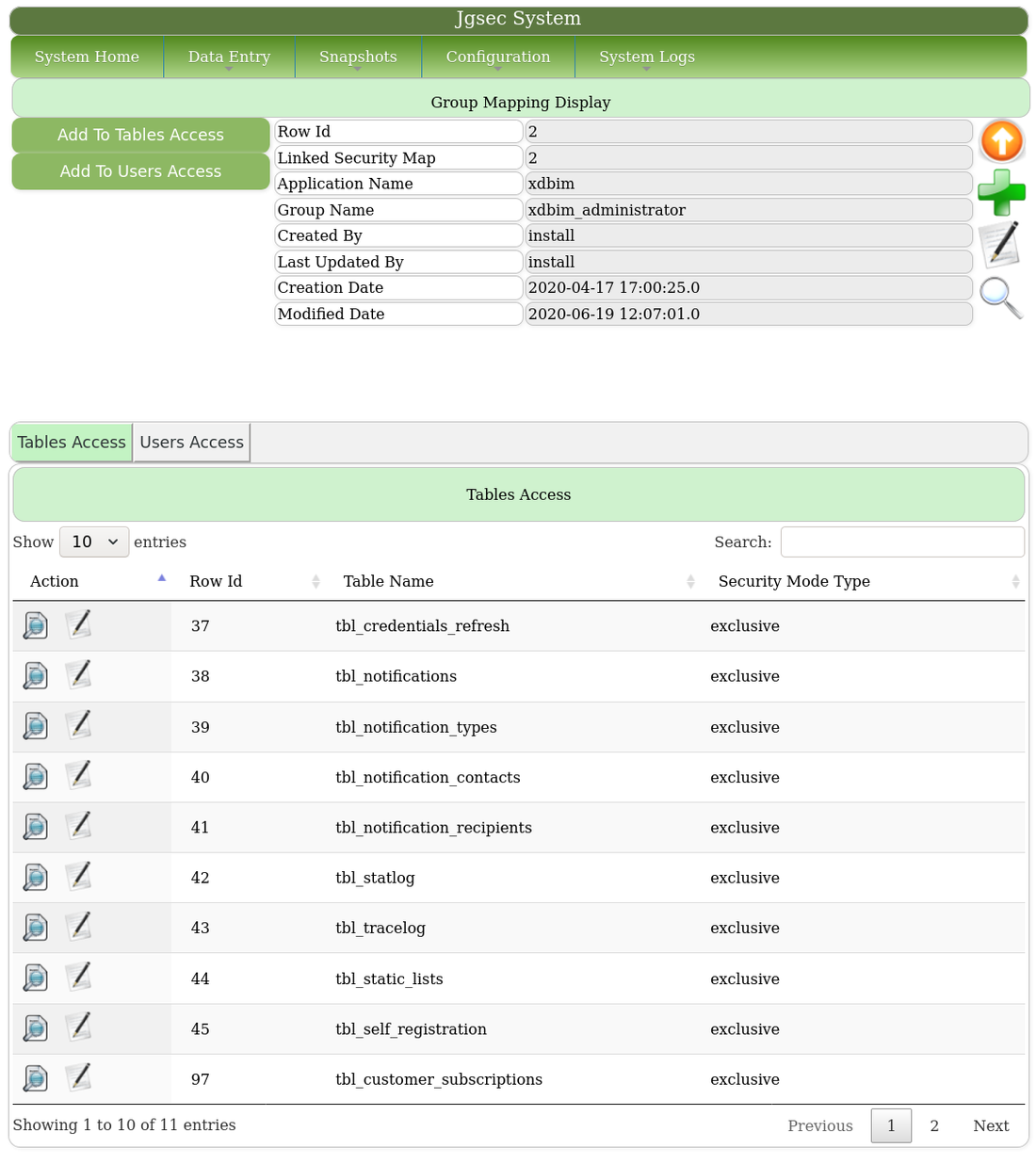
This shows group membership.
Submitter mode on a table means access permissions apply to all users irrespective of group membership. If the submitter mode is set as inclusive, all system users have read-only rights to the table. If the submitter mode is set to exclusive, all system users have read-write access to the table.
Submitter mode can be applied to tables that store reference data, for example, that all users may read, but may not change. This will be Submitter Inclusive.
Submitter mode may also be applied to tables where each user owns their own data to the exclusion of all other users. This will be Submitter Exclusive.
Submitter Exclusive is an access mode that effectively grants user multi-tenancy to a table.
Navigate to "Configuration"-"Users List".
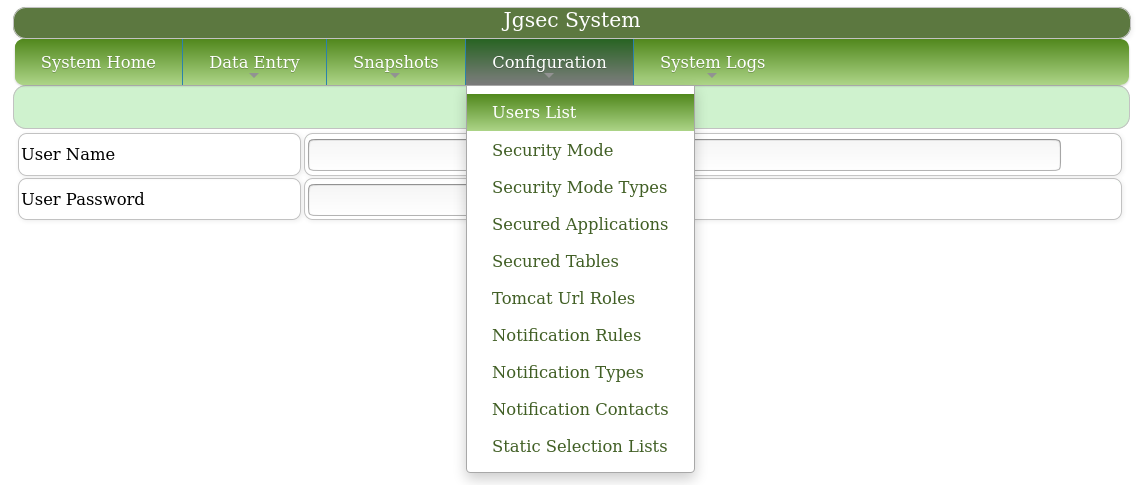
Add the user.
The added user then becomes available to be assigned to table permissions.
Navigate to "Security Map"-"Group Map" and select "Add to User Access". Select the newly added user to be assigned to the group. When added, this user has access to all the tables listed in the Group Map.
 Managing Users and Security
Managing Users and Security


